AI-Powered Cybersecurity: How Machine Learning is Revolutionizing Digital Defense in 2025
Table of Contents
Discover how AI and machine learning are transforming cybersecurity in 2025. Learn about threat detection, automated responses, emerging trends, and implementation strategies for robust digital defense.
The cybersecurity landscape in 2025 has reached a critical inflection point where artificial intelligence serves as both the ultimate shield and the most formidable sword. As organizations worldwide grapple with increasingly sophisticated cyber threats, AI-powered cybersecurity solutions have emerged as the decisive factor in determining who wins the digital arms race.
According to recent industry reports, 95% of organizations agree that AI-powered cybersecurity solutions significantly improve the speed and efficiency of prevention, detection, response, and recovery. This dramatic shift represents more than just technological advancement—it’s a fundamental reimagining of how we approach digital defense in an era where traditional security measures are becoming obsolete.
The Current State of AI in Cybersecurity: A 2025 Perspective
The integration of artificial intelligence into cybersecurity has accelerated beyond all predictions. More than 90% of AI capabilities in cybersecurity are expected to come from third-party providers, making cutting-edge AI security solutions accessible to organizations of all sizes. This democratization of AI-powered defense tools has leveled the playing field, allowing smaller companies to deploy enterprise-grade security measures.
Pro Tip: Organizations implementing AI cybersecurity solutions should prioritize integration capabilities with existing security infrastructure to maximize ROI and minimize deployment complexity.
The Numbers Tell the Story
The statistics from 2025 paint a clear picture of AI’s growing dominance in cybersecurity:
- 87% of global organizations have faced an AI-powered cyber attack in the past year
- 72% of Indian organizations reported being targeted by AI-powered cyberattacks
- Only 14% felt truly prepared to deal with these AI-enhanced threats
- AI-driven cybersecurity solutions are expected to save organizations over $150 billion annually through enhanced threat detection and prevention
How Machine Learning is Transforming Threat Detection
Real-Time Pattern Recognition and Anomaly Detection
Machine learning algorithms excel at processing vast amounts of data to identify patterns that would be impossible for human analysts to detect. AI-powered systems can detect threats in real-time, enabling rapid response and mitigation. These systems continuously learn from network traffic, user behavior, and system logs to establish baseline patterns and immediately flag deviations.
Key Advantage: Unlike traditional signature-based detection systems, ML models can identify zero-day attacks and novel threat vectors by recognizing suspicious behavioral patterns rather than relying on known threat signatures.
Predictive Threat Analytics
The shift from reactive to proactive cybersecurity represents one of 2025’s most significant developments. AI-powered predictive analytics is helping organizations identify potential vulnerabilities and anticipate attack vectors before they can be exploited. This proactive approach enables security teams to:
- Predict potential system vulnerabilities based on historical data
- Anticipate attack patterns using trend analysis
- Allocate resources more effectively to high-risk areas
- Implement preventive measures before threats materialize
Automated Incident Response
Perhaps the most transformative aspect of AI in cybersecurity is its ability to respond to threats autonomously. AI can instantly analyze an attack, isolate compromised systems, and neutralize threats, significantly reducing response times. This automation is crucial given that attackers exploit flaws within hours of vulnerability disclosure, with the average time for exploitation now just eight days.
The Dual Nature of AI: Defense and Offense
AI-Enhanced Cyber Threats
While AI strengthens cybersecurity defenses, it simultaneously empowers cybercriminals with unprecedented capabilities. New AI tools like WormGPT and FraudGPT are making it easier for even inexperienced hackers to launch serious cyber attacks. These tools enable cybercriminals to:
The Arms Race Intensifies
Searches for “AI cyber attacks” have increased by 186% in the last 2 years, reflecting growing concern about AI-powered threats. Cybercriminals are leveraging AI to:
- Generate convincing phishing emails that bypass traditional filters
- Create malware that adapts to security defenses in real-time
- Automate reconnaissance and vulnerability discovery
- Scale attacks across multiple targets simultaneously
Note: Organizations must understand that implementing AI cybersecurity isn’t optional—it’s essential for survival in the current threat landscape.
Key AI Applications Revolutionizing Cybersecurity
1. Behavioral Analysis and User Authentication
AI systems analyze user behavior patterns to detect potential insider threats and compromised accounts. Machine learning models continuously learn from vast volumes of data to identify patterns and anomalies in real time, enabling organizations to:
2. Network Security and Traffic Analysis
ML algorithms excel at analyzing network traffic to identify malicious activities:
- DDoS attack prevention: Models analyze traffic patterns to predict and prevent distributed denial-of-service attacks
- Botnet detection: AI identifies coordinated malicious activities across network endpoints
- Lateral movement detection: Systems track unusual data flows that indicate compromised networks
3. Malware Detection and Analysis
Traditional signature-based antivirus solutions struggle against modern threats, but AI-powered detection systems offer superior capabilities:
- Zero-day malware detection: ML models identify malicious code based on behavioral patterns rather than signatures
- Polymorphic malware analysis: AI tracks malware that changes its code to evade detection
- Reverse engineering automation: Systems automatically analyze malware to understand attack vectors
Implementation Challenges and Solutions
Integration with Legacy Systems
One of the primary challenges organizations face is integrating AI-powered security solutions with existing infrastructure. Traditional defenses like basic antivirus solutions, firewalls and intrusion prevention systems will fall short in addressing the advanced AI-powered cyber threats.
Solution Strategy:
- Implement AI solutions as overlay systems that enhance rather than replace existing tools
- Use APIs and integration platforms to connect AI analytics with traditional security tools
- Gradually migrate to AI-native security platforms as budget and timing allow
Skills Gap and Training Requirements
The cybersecurity industry faces a significant skills shortage, particularly in AI and machine learning applications. Organizations must invest in:
- Training existing security personnel on AI tools and methodologies
- Recruiting specialists with both cybersecurity and AI expertise
- Partnering with managed security service providers (MSSPs) that offer AI-powered services
- Implementing user-friendly AI tools that require minimal specialized knowledge
Data Quality and Privacy Concerns
AI systems require high-quality data to function effectively, but organizations often struggle with:\
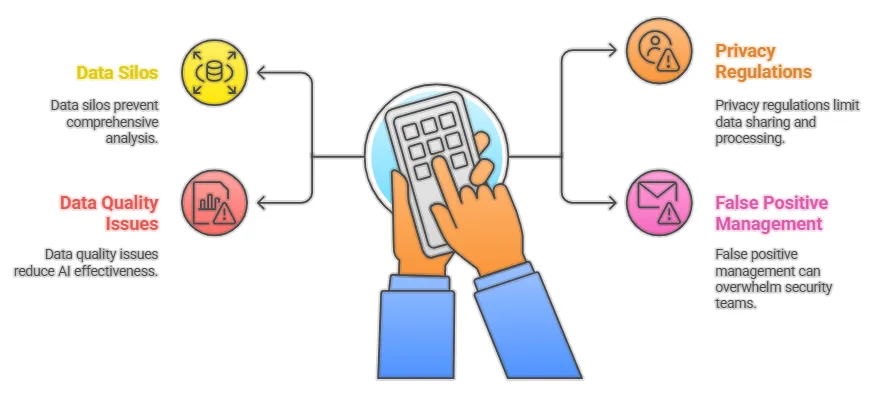
- Data silos that prevent comprehensive analysis
- Privacy regulations that limit data sharing and processing
- Data quality issues that reduce AI effectiveness
- False positive management that can overwhelm security teams
Emerging Trends Shaping the Future
Quantum-Resistant AI Security
As quantum computing advances, quantum computing has the potential to break contemporary encryption. Forward-thinking organizations are already implementing quantum-resistant algorithms and AI systems designed to operate in a post-quantum world.
Zero Trust Integration
Zero trust becomes the new hot thing as perimeter-based security becomes obsolete. AI plays a crucial role in zero trust architectures by:
- Continuously validating user and device identities
- Analyzing contextual factors for access decisions
- Implementing micro-segmentation based on AI-driven risk assessments
- Monitoring for lateral movement and privilege escalation
Autonomous Security Operations
The future points toward fully autonomous security operations centers where AI agents could soon work alongside humans in a semi-autonomous manner to identify, think through, and dynamically execute tasks such as alert triage, investigation, response actions, or threat research.
Regional Implementation Landscape
Pro Tips for Successful AI Cybersecurity Implementation
1. Start with High-Impact Use Cases
Focus initial AI implementations on areas with the highest potential impact:
2. Establish Clear Metrics
Define success metrics before implementation:
- Mean time to detection (MTTD)
- Mean time to response (MTTR)
- False positive rates
- Cost per incident
- User satisfaction scores
3. Maintain Human Oversight
While AI automation is powerful, human expertise remains essential:
- Implement human-in-the-loop systems for critical decisions
- Regular model validation and tuning
- Continuous training and skill development
- Escalation procedures for complex incidents
4. Focus on Data Quality
Use high-quality data, regularly update models, maintain human oversight, ensure transparency, and foster collaboration between AI and human analysts:
- Implement data governance frameworks
- Regular data cleaning and validation
- Diverse data sources for comprehensive coverage
- Privacy-preserving techniques where required
Frequently Asked Questions
Q: How quickly can AI cybersecurity systems detect threats?
A: Modern AI systems can detect threats in milliseconds to seconds, compared to days or weeks for traditional systems. AI-powered systems can detect threats in real-time, enabling rapid response and mitigation, with some advanced systems achieving detection times under 100 milliseconds for known attack patterns.
Q: What’s the ROI of implementing AI cybersecurity solutions?
A: Organizations typically see ROI within 12-18 months through reduced incident response costs, faster threat detection, and prevention of major breaches. AI-driven cybersecurity solutions are expected to save organizations over $150 billion annually by 2025 through enhanced threat detection and prevention.
Q: Can small businesses afford AI-powered cybersecurity?
A: Yes, more than 90% of AI capabilities in cybersecurity are expected to come from third-party providers, making AI security accessible through cloud-based services and managed security providers. Many solutions are now available as affordable SaaS offerings.
Q: How does AI handle zero-day attacks?
A: AI systems excel at detecting zero-day attacks because they identify suspicious behavioral patterns rather than relying on known threat signatures. This behavioral analysis allows AI to detect previously unknown threats based on anomalous activities.
Q: What are the main risks of using AI in cybersecurity?
A: Key risks include false positives overwhelming security teams, AI model bias, adversarial attacks against AI systems, and over-reliance on automation. However, best practices include using high-quality data, regularly updating models, maintaining human oversight, ensuring transparency.
Q: How do AI-powered attacks differ from traditional cyber attacks?
A: AI-powered attacks are more sophisticated, adaptive, and scalable. AI can adapt ransomware files over time, reducing their detectability and improving their efficacy. They can automatically adjust tactics based on defensive responses and operate at machine speed.
Q: What skills do cybersecurity professionals need for AI implementation?
A: Essential skills include understanding of machine learning concepts, data analysis, AI tool configuration, and the ability to interpret AI-generated insights. However, many modern AI security tools are designed to be user-friendly and don’t require deep technical AI expertise.
Q: How should organizations prepare for quantum computing threats?
A: Organizations should begin implementing quantum-resistant encryption algorithms and AI systems designed for post-quantum security. Latest trends in cyber security discussions lead to quantum-resistant algorithms for critical data, with early adoption providing protection when quantum computers mature.
The Road Ahead: 2025 and Beyond
The cybersecurity landscape in 2025 represents a fundamental shift toward AI-powered defense strategies. This report serves as a wake-up call that cybersecurity can no longer be an afterthought. It must be embedded by design into every AI-driven initiative. Organizations that embrace AI cybersecurity solutions position themselves not just to survive but to thrive in an increasingly hostile digital environment.
The convergence of AI and cybersecurity has created unprecedented opportunities for both defenders and attackers. Success in this new landscape requires a strategic approach that combines cutting-edge AI technology with human expertise, robust data governance, and continuous adaptation to emerging threats.
As we move forward, the organizations that will emerge as leaders are those that view AI cybersecurity not as a technology investment but as a fundamental business capability. The question is no longer whether to implement AI-powered cybersecurity solutions, but how quickly and effectively organizations can adapt to this new reality.
Key Takeaway: The future of cybersecurity is AI-powered, and the time for implementation is now. Organizations that delay adoption risk falling behind in the rapidly evolving threat landscape, while those that embrace AI-driven security solutions gain significant competitive advantages in protecting their digital assets and maintaining customer trust.
IF YOU REACH AT END, GO GIVE A LOOK AT blogs ON OUR MAIN website.