Cybersecurity Mesh Architecture: The Future-Proof Security Framework for Remote Work Environments 25

Table of Contents
Cybersecurity Mesh Architecture transforms remote work security with distributed controls, zero trust principles, and scalable protection for modern enterprises.
The remote work revolution has shattered traditional security boundaries forever. While 73% of organizations now support hybrid work models, their cybersecurity strategies remain trapped in the pre-pandemic era of castle-and-moat defenses.
The stark reality? Cybersecurity incidents have surged 22% globally in 2024, with state-sponsored groups like Volt Typhoon exploiting the vulnerabilities of distributed workforces. Traditional perimeter-based security simply can’t protect employees working from coffee shops, home offices, and co-working spaces across the globe.
Enter Cybersecurity Mesh Architecture (CSMA) – a revolutionary approach that wraps security around every individual user, device, and access point rather than trying to defend a single corporate boundary. This isn’t just another security trend; it’s a fundamental shift toward identity-centric, distributed protection that grows with your organization.
The Current Remote Work Security Crisis
Market Growth Reflects Urgent Need
The cybersecurity mesh market tells a compelling story of urgent adoption. Valued at $2.59 billion in 2024, the market is projected to explode to $7.03 billion by 2033, growing at an impressive 11.9% CAGR. This isn’t speculative growth – it’s driven by immediate business necessity.
💡 Pro Tip: Companies implementing early CSMA frameworks have cut breach exposure by 68% compared to traditional perimeter-centric designs.
Why Traditional Security Fails Remote Workers

The shift to distributed work has exposed critical flaws in conventional security models:
- Assets live everywhere: Applications span multiple clouds, employees connect from countless locations, and devices operate outside corporate networks
- Threats are more sophisticated: Advanced persistent threats (APTs), AI-enabled attacks, and zero-day vulnerabilities specifically target remote work vulnerabilities
- Perimeter doesn’t exist: The traditional “inside vs. outside” network concept becomes meaningless when your “inside” includes thousands of home networks
📝 Note: Organizations still relying on VPN-based remote access report 40% higher security incidents than those implementing mesh-based architectures.
Technical Deep Dive: How Cybersecurity Mesh Works
Core Architecture Principles
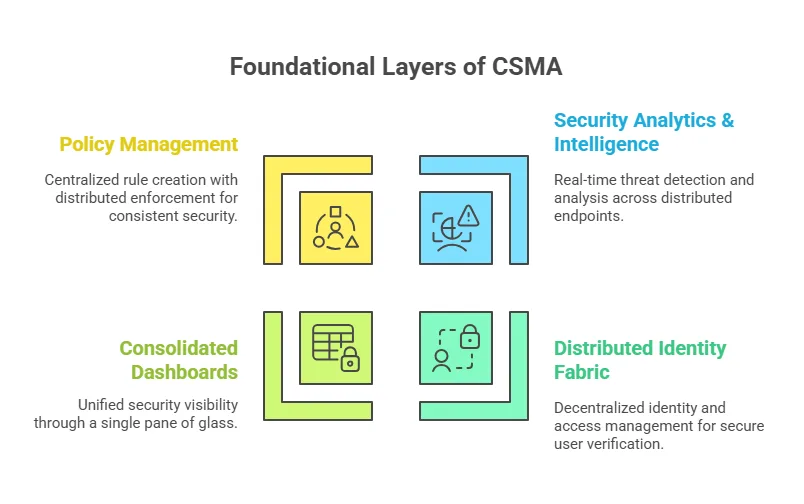
CSMA operates on four foundational layers that work together to create a “collaborative ecosystem of tools and controls”:
The Technical Magic: Separation of Concerns
Unlike traditional models where policy creation and enforcement happen in the same place, CSMA separates policy orchestration from policy enforcement. This means:
- Centralized brain: Security teams create consistent rules from a single location
- Distributed muscle: Each device, application, and network segment enforces those rules locally
- Dynamic adaptation: Policies adjust in real-time based on context, risk, and behavior
⚠️ Important: This architectural separation enables organizations to maintain centralized control while allowing distributed and localized policy implementation.
Zero Trust Integration
CSMA aligns perfectly with Zero Trust principles by implementing “never trust, always verify” at scale. Rather than trusting anything inside a network perimeter, mesh architecture:
- Continuously authenticates every user and device
- Applies microsegmentation to limit lateral movement
- Monitors all network traffic for anomalies
- Enforces least-privilege access consistently
Real-World Applications: CSMA in Action
Financial Services: Multi-Cloud Protection
Major financial institutions are leveraging CSMA to secure trading floors, customer portals, and regulatory reporting systems across hybrid environments. The architecture enables:
- Fraud prevention: Real-time analysis of user behavior patterns across all touchpoints
- Regulatory compliance: Granular access controls that meet SOX, PCI-DSS, and regional requirements
- Customer data protection: Encryption and monitoring that follows data wherever it travels
Healthcare: Securing Patient Data Everywhere
Healthcare organizations face unique challenges with HIPAA compliance, IoT medical devices, and telemedicine platforms. CSMA addresses these through:
- Device-level protection: Every connected medical device gets its own security perimeter
- Patient privacy: Data encryption and access controls that work across multiple cloud providers
- Compliance automation: Continuous monitoring and reporting for audit requirements
Manufacturing: Supply Chain Security
Modern manufacturing involves complex supply chains with partners, suppliers, and distributed facilities. CSMA provides:
- Intellectual property protection: Securing design files and proprietary processes across the entire ecosystem
- IoT security: Protection for industrial control systems and smart manufacturing equipment
- Partner access control: Granular permissions for external collaborators without compromising security
💡 Pro Tip: Manufacturing companies report 45% faster incident response times after implementing mesh architectures, thanks to distributed detection capabilities.
Government: Critical Infrastructure Protection
Government agencies use CSMA to secure:
- Classified information: Multi-level security that adapts to clearance levels and need-to-know requirements
- Inter-agency collaboration: Secure information sharing without compromising individual agency security
- Critical infrastructure: Protection for power grids, transportation systems, and emergency services
Market Analysis & Investment Trends
Explosive Growth Across All Sectors
Multiple market research firms project substantial growth for cybersecurity mesh solutions:
📝 Note: While projections vary, all major analysts agree on double-digit growth driven by remote work security needs and zero trust adoption.
Key Investment Drivers
The market surge is fueled by several converging factors:
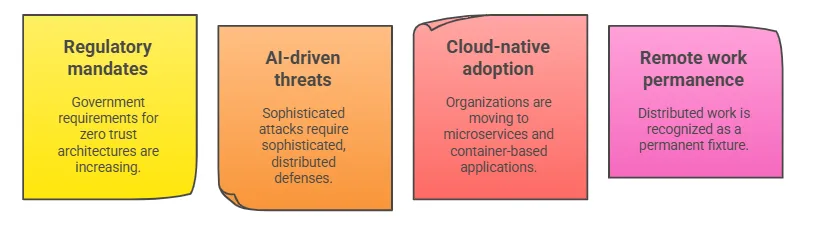
- Regulatory mandates: Increasing government requirements for zero trust architectures
- AI-driven threats: Sophisticated attacks that require equally sophisticated, distributed defenses
- Cloud-native adoption: Organizations moving to microservices and container-based applications
- Remote work permanence: Recognition that distributed work is here to stay
Regional Adoption Patterns
North America leads adoption with a 36% market share in 2024, driven by strict regulatory requirements and early zero trust mandates. However, Asia-Pacific shows the fastest growth as organizations leapfrog traditional security models entirely.
Implementation Roadmap: Building Your Mesh
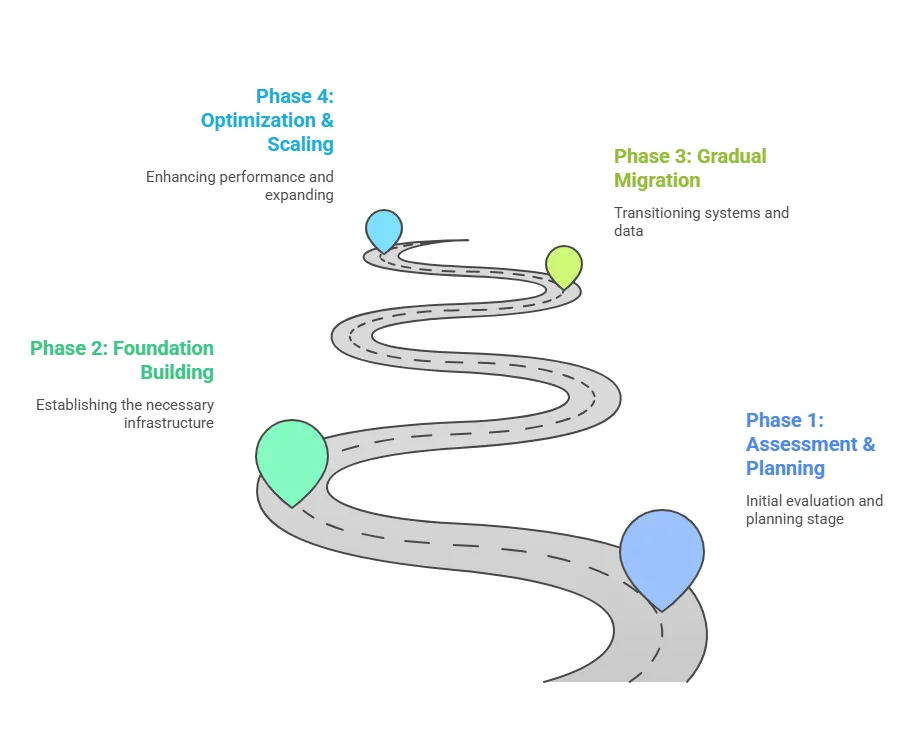
Phase 1: Assessment & Planning (Months 1-2)
💡 Pro Tip: Start with an asset protection inventory to understand your current security tool maturity and integration capabilities.
Key activities include:
- Mapping all devices, users, and access points
- Evaluating existing security tool integration capabilities
- Assessing organizational appetite for change
- Identifying high-risk areas requiring immediate protection
Phase 2: Foundation Building (Months 3-6)
Begin with core infrastructure components:
- Identity fabric deployment: Implement centralized identity management across all environments
- Policy framework creation: Develop consistent rules that can be enforced anywhere
- Analytics platform setup: Deploy tools for continuous monitoring and threat detection
⚠️ Important: Choose security solutions with open policy frameworks to ensure flexibility and customization.
Phase 3: Gradual Migration (Months 6-18)
📝 Note: Most successful implementations follow a phased approach rather than attempting big-bang transitions.
- Start with highest-risk assets and users
- Implement microsegmentation for critical applications
- Deploy distributed enforcement points
- Integrate existing security tools into the mesh framework
Phase 4: Optimization & Scaling (Ongoing)
- Continuous monitoring and policy refinement
- Integration of new tools and technologies
- Staff training and skill development
- Regular security posture assessments
Common Implementation Challenges & Solutions
Challenge 1: Legacy System Integration
The Problem: Many organizations struggle to integrate existing security tools into a mesh framework.
The Solution: Focus on solutions with open APIs and standardized protocols. Consider a hybrid approach where legacy systems operate alongside mesh components until full migration is possible.
Challenge 2: Skills Gap
The Problem: CSMA requires new skills and understanding from security teams.
The Solution: Invest in training programs and consider managed security services for initial implementation phases.
Challenge 3: Complexity Management
The Problem: Distributed security can seem more complex than centralized models.
The Solution: Start small with pilot programs and gradually expand. Use automation and AI to manage complexity.
💡 Pro Tip: Organizations report that while initial CSMA setup may be complex, ongoing management becomes simpler than traditional security models once properly implemented.
Future Outlook: What’s Coming Next
AI-Driven Policy Orchestration
The next evolution of CSMA will leverage artificial intelligence for:
- Predictive threat modeling: Anticipating attacks before they happen
- Automated policy adjustment: Real-time rule changes based on threat landscape
- Behavioral analytics: Understanding normal patterns to identify anomalies faster
5G and Edge Computing Integration
As 5G networks enable massive IoT deployments, CSMA will evolve to support:
- Micro-segmentation at scale: Protecting millions of connected devices
- Edge-based enforcement: Security processing closer to data sources
- Ultra-low latency protection: Real-time security that doesn’t slow applications
Regulatory Evolution
Expect increasing government mandates around:
- Zero trust adoption: Federal requirements driving private sector implementation
- Data localization: Mesh architectures that respect geographic data sovereignty
- Supply chain security: Protection requirements for vendor and partner access
Frequently Asked Questions
Q: How does cybersecurity mesh impact network performance?
A: When properly implemented, CSMA should have minimal performance impact and may actually improve performance by reducing bottlenecks associated with centralized security controls.
Q: Can cybersecurity mesh work alongside existing security solutions?
A: Yes, CSMA is designed to integrate with existing security tools and often enhances their effectiveness by providing a framework for better interoperability.
Q: What’s the typical implementation timeline for CSMA?
A: Most organizations see initial benefits within 3-6 months, with full implementation taking 12-18 months depending on complexity and existing infrastructure.
Q: How much does cybersecurity mesh implementation cost?
A: Costs vary significantly based on organization size and complexity, but many organizations find CSMA reduces overall security costs by optimizing resource allocation and improving efficiency.
Q: Is CSMA suitable for small businesses?
A: While originally designed for enterprises, cloud-based CSMA solutions are making the approach accessible to organizations of all sizes.
Q: How does CSMA handle compliance requirements?
A: CSMA actually simplifies compliance by providing granular control and continuous monitoring that makes audit preparation much easier.
Q: What role does artificial intelligence play in cybersecurity mesh?
A: AI enhances CSMA by improving threat detection, automating policy adjustments, and providing predictive analytics to identify patterns that indicate security risks.
Q: Can CSMA protect against insider threats?
A: Yes, by implementing continuous monitoring and zero trust principles, CSMA can detect unusual behavior patterns that may indicate insider threats.
The future of remote work security isn’t about building higher walls – it’s about making security as distributed and adaptable as your workforce. Cybersecurity Mesh Architecture doesn’t just protect your organization; it enables the kind of flexible, secure collaboration that drives competitive advantage in our distributed world.
Ready to future-proof your remote work security? The mesh revolution has begun, and early adopters are already seeing the benefits. The question isn’t whether you’ll implement CSMA – it’s whether you’ll lead the transformation or scramble to catch up.
IF YOU REACH AT END, GO GIVE A LOOK AT blogs ON OUR MAIN website.